Evolving VPN-based Services: A Framework for Enhanced VPNs
Virtual Private Networks (VPNs) have become one of the most sold network services offered by Internet Service Providers (ISPs). They provide connectivity between remote customer sites; the technology allows computers within the customer’s network to communicate as though they were all attached to the same local physical network. That is, the VPN service builds a private network for the customer.
This type of service was once achieved using dedicated physical connectivity, but that was, of course, expensive. The VPN delivers the service over a shared infrastructure (the ISP’s network or Internet) by multiplexing connectivity on the network links, allowing site-to-site communication between regional offices as shown in Figure 1 VPN Topology Example below. Thus the network created for the customer is virtual.
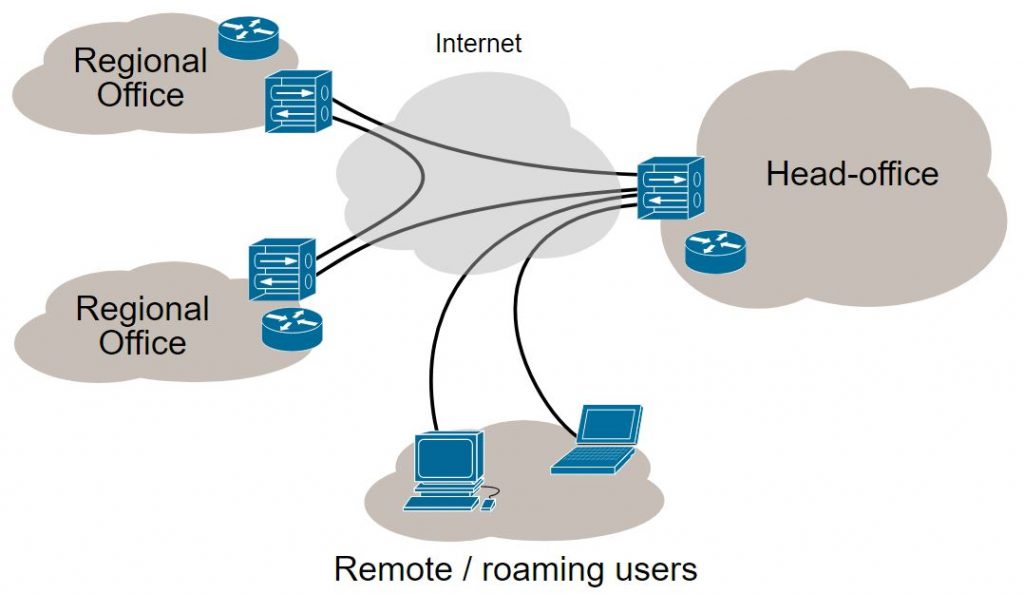
Figure 1 : VPN Topology
Customer connectivity can be offered at the IP layer, in what is called a Layer 3 VPN (L3VPN) service, or at a lower layer to provide a Layer 2 VPN (L2VPN) service. These days, most L2VPNs offer Ethernet connectivity.
ISPs can use several different technologies to deliver VPN services depending on the protocols deployed in the ISP’s network. It is widespread to use the Border Gateway Protocol (BGP) to exchange VPN membership information between ISP edge points (the Provider Edge nodes – PEs), although Software Defined Networking (SDN) techniques can also be used to programme the information into the PEs. The connectivity between the PEs is provided by tunnels, and these can be IP-in-IP, IPsec, MPLS, or Segment Routing (SR) depending on the way the ISP chooses to run their network and the VPN service being offered.
While VPNs have been hugely successful, they do have some drawbacks. In particular, because the various VPNs share the ISP’s network infrastructure, the traffic from one VPN can “interfere” with the traffic on another VPN effectively threatening the Service Level Agreement (SLA) promised by the ISP to the customer. For example, a massive burst of traffic between two sites in VPN-A may congest some of the links in the ISP’s network resulting in delays or even packet loss for traffic travelling between sites in VPN-B where that traffic happens to use the same links in the ISP’s network.
Furthermore, the standard VPN service typically offers connectivity at certain data rates. That allows the ISP to use shortest path routing or its own traffic engineering algorithms to distribute traffic flows within its network. However, many new applications demand additional qualities to the VPN service such as low latency between the VPN sites, or well-bounded delay variation (jitter).
What is required for legacy VPN-based services was an evolution to address the more dynamic nature of Enterprise services and next generation Internet applications; this has lead to the development of enhanced VPNs.
Enhanced VPNs
An enhanced VPN (sometimes referred to as VPN+) is a VPN service with additional service guarantees. The advanced functions that a VPN service may request include:
- Isolation between enhanced VPNs. Isolation is a feature offered by a network operator where the traffic from one service instance is isolated from the traffic of other services. There is a spectrum of grades of isolation that is ranging from simple separation of traffic on delivery to the customers (known as soft isolation) to complete separation within the underlying network so that the traffic from different services use distinct network resources (known as hard isolation).
- Performance Guarantees. A customer negotiating with a service provider for a VPN service may ask for performance guarantees such as throughput, maximum packet loss, maximum delivery delay, and limits to the variation in end-to-end delay. One or more of these guarantees may be agreed for any individual service.
- Virtual Networks and Abstraction. A Virtual Network (VN) is a type of service that connects customer edge points with the additional possibility of requesting further service characteristics in the manner of an enhanced VPN. A VN allows the customer to act as though they had a genuine, private network connecting their sites. Abstraction [1] is the process of applying policy to information about a TE network to produce a selective representation of the potential ability to connect across the network. This produces a connectivity graph that is independent of the underlying network technologies, capabilities, and topology so that the graph can be used to plan and deliver network services as a VN.
- Dynamic Configuration and Customised Control. A customer’s demands for their VPN service may vary over time. For example, they may want to add or remove sites from the VPN, or to vary the capacity or other performance characteristics. An essential attribute of how the VPN+ service is delivered is that it can be dynamically configured “under the feet” or the running service without disrupting traffic. Moreover, of course, if isolation of services is in play, changes to one enhanced VPN must not be detectable by the users of other enhanced VPNs. Additionally, if the enhanced VPN is exposed as a virtual network, the customer may wish to operate and control the network as though it was their own private network.
- Multi-Domain Deployment. While some enhanced VPN services will be supported by single service provider domains, others will span multi-domain service providers, and may even need to be supported by domains owned and operated by different service providers. Furthermore, these domains might not all utilise the same network technologies. An enhanced VPN needs to provide a service that is agnostic to the technologies used to deliver it and to the network domains that support it.
The Internet Engineering Task Force (IETF) is specifying “A Framework for Enhanced Virtual Private Networks (VPN+) Service” [2]. This framework identifies the additional features of a VPN service demanded by advanced applications (as above), identifies some key use cases for VPN+ (as below), and examines some of the existing and up-coming technologies that could be used to deliver the services.

Applications of Enhanced VPNs
While regarding an enhanced VPN as a potentially attractive service, the deployment of new technologies and management systems must be predicated on sound business prospects. Three broad categories of customer service can be realised through the use of enhanced VPNs.
- Advanced Applications. A number of future services and applications are being considered in the light of the new 5G technology. These include virtual reality conferencing, crowd-sourced video streaming, and multi-party gaming. Each needs a number of sites to be linked with specific requirements for network performance and so is a good candidate to be addressed using VPN+.
- Virtual Networks. Many enterprise network operators are looking beyond simple connectivity between their sites. They want to be able to control how their traffic is routed, and to be able to modify the behaviour of the virtual links over which their traffic flows in exactly the same way that they would if they owned private connectivity. The enhanced VPN offers this increased level of flexibility.
- Network Slicing. The concept of network slicing is much discussed within the 5G world. An Internet-Draft in the IETF [3], defines a Network Slice as an agreement between a consumer and a service provider to deliver network resources according to a specific service level agreement. It goes on to define a transport network slice as a construct to provide an end-to-end logical network, often with compute functions and utilising shared underlying (physical or virtual) network resources. This logical network is separated from other, often concurrent, logical networks, each with independent control and management, and each of which can be created or modified on demand. Clearly an enhanced VPN is a tool for delivering a network slice.
An ACTN Solution for VPNs
Abstraction and Control of TE Networks (ACTN) [4] is a management architecture that allows a customer to request a connectivity service (such as a VPN or enhanced VPN) and have the service expressed as a virtual network or network slice. The architecture is recursive so that the enhanced VPN may be constructed from several different networks of differing technologies, yet enabling it to be presented to the customer as a simple topology.
ACTN has been identified as a suitable approach for delivering enhanced VPNs [2]. As shown in Figure 2, the ACTN components can be used to request, deliver, and control the enhanced VPNs. The Customer Network Controllers (CNCs) determines what services the customer wants, and makes requests to the Multi-Domain Service Controller (MDSC) in the provider’s network. The MDSC is aware of the various physical networks that are available, and determines the best way to meet the customer’s demands. The MDSC is then able to instruct the Physical Network Controllers (PNCs) to configure and provision the elements in the physical networks. This effectively dedicates connections and resources (slices the networks) for use by the enhanced VPNs. The PNCs report to the MDSC which, in turn reports to the CNCs. Also, the CNCs are now able to control the enhanced VPNs.

Figure 2 : The ACTN Architecture Used to Deliver Enhanced VPNs
Relevance to METRO-HAUL
The aim of the METRO-HAUL project is to design and build a smart optical metro infrastructure able to support traffic originating from heterogeneous 5G access networks, addressing the anticipated capacity increase and its specific characteristics. This infrastructure will also support a wide variety of services and use cases with special emphasis on services from various industries vertical to the ICT.
This will be achieved by architecting new access-facing and core-facing nodes, complete with storage and compute facilities, interconnected by a novel, spectrally efficient, and adaptive optical transmission networks. Advanced concepts, such as hardware disaggregation and virtualisation, will assist in hitting challenging cost targets while enabling automation and programmability – all supported by a purpose-designed SDN-based control plane which will interface with client applications, intelligently catering for the full range of 5G KPIs.
This software-based (SDN) control architecture is based on ACTN [5]. Using a standards-based architecture has many advantages for the project not least of which is access to innovative technology developments and development of open-source software.
Network slicing has been discussed extensively within the METRO-HAUL project [6]. It’s relevance to 5G networks and to the transport networks that support 5G makes it an important concept for the project. It is applicable to all of the use cases and demonstrations that are being worked on within METRO-HAUL and allows (for example) bandwidth to be dynamically reserved for service-critical traffic without having an impact on other services that the network may be carrying.
Recognising the value of network slicing, partners in METRO-HAUL are contributing to the IETF’s work on enhanced VPNs [2] with a view to ensuring that that the ideas and innovation developed within the project are made available to the wider networking community.
References
[1] Problem Statement and Architecture for Information Exchange between Interconnected Traffic-Engineered Networks, RFC 7926, July 2016, https://www.rfc-editor.org/rfc/rfc7926.txt
[2] A Framework for Enhanced Virtual Private Networks (VPN+) Service, work in progress, https://www.ietf.org/id/draft-ietf-teas-enhanced-vpn
[3] Applicability of Abstraction and Control of Traffic Engineered Networks (ACTN) to Network Slicing, work in progress, https://www.ietf.org/archive/id/draft-king-teas-applicability-actn-slicing
[4] Framework for Abstraction and Control of TE Networks (ACTN), RFC 8453, August 2018, https://www.rfc-editor.org/rfc/rfc8453.txt
[5] What is ACTN? – A METRO-HAUL blog, August 2018, https://metro-haul.eu/2018/08/30/what-is-actn/
[6] To Slice or Not to Slice, That is the Question – A METRO-HAUL blog, November 2017, https://metro-haul.eu/2017/11/08/to-slice-or-not-to-slice-that-is-the-question/




